
Microsoft researchers have discovered a Windows-Linux hybrid botnet that uses a highly efficient technique to bring it down Minecraft server and performs distributed denial-of-service attacks on other platforms.
Dubbed MCCrash, the botnet infects Windows machines and devices running various distributions of Linux for use in DDoS attacks. Among the commands accepted by the botnet software is one called ATTACK_MCCRASH. This command populates the username in a Minecraft server login page with ${env:random payload of specific size:-a}. The string exhausts the server’s resources and causes it to crash.
Microsoft
“The use of env variable triggers the use of the Log4j 2 library, which causes abnormal consumption of system resources (unrelated to the Log4Shell vulnerability), demonstrating a specific and highly efficient DDoS method,” Microsoft researchers wrote. “A wide range of versions of the Minecraft server may be affected.”
Currently, MCCrash is hardcoded to target version 1.12.2 only Minecraft server software. The attack technique, however, will block servers running versions 1.7.2 through 1.18.2, which handle about half of the Minecraft server. If the malware is updated to target all vulnerable versions, its reach could be much wider. A change in Minecraft server version 1.19 prevents the attack from working.
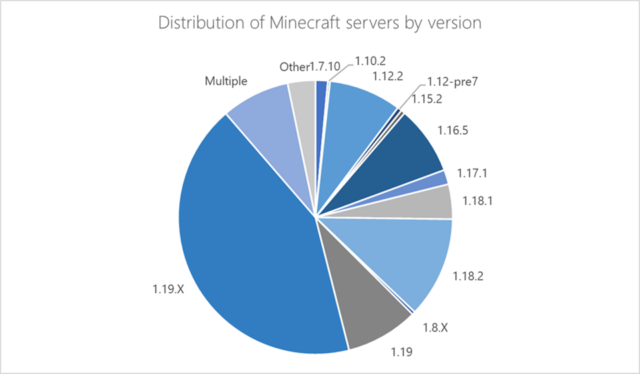
“The wide range of subjects at risk Minecraft server highlights the impact this malware could have had had it been specifically coded to affect versions later than 1.12.2,” Microsoft researchers wrote. part of the botnet substantially increases its impact and reduces its chances of being detected.”
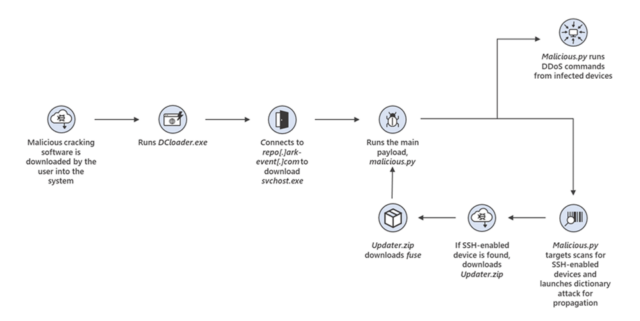
The initial infection point for MCCrash is Windows machines that have software installed that claims to provide pirated licenses for the Microsoft operating system. Code hidden in downloaded software surreptitiously infects the device with malware that installs malign.py, a Python script that provides the core logic for the botnet. Infected Windows devices then scan the internet for Debian, Ubuntu, CentOS and IoT devices that accept SSH connections.
Microsoft
Once found, MCCrash uses the common default login credentials in an attempt to run the same malign.py script on the Linux device. Both Windows and Linux devices are therefore part of a botnet running the Minecraft attack as well as other forms of DDoS. The graph below shows the attack flow.
Microsoft
A breakdown of MCCrash-infected devices shows that most of them are located in Russia. Microsoft hasn’t said how many devices are infected. Company researchers said they believe botnet operators are using it to sell DDoS services on criminal forums.